Reliability and Security
Large-scale data breaches continue to expose the weaknesses in traditional information security strategies. Network and device protection is clearly not enough. Full-disk or volume encryption is a single-use-case approach that leaves information exposed at the data level. Persistent data-level encryption has become a necessity, especially in highly regulated industries.
Trusted By
Top Organizations for 40+ Years
Benefits of SecureZIP
Modernize Your Data Strategy With PK Protect
Secure, Automate, and Simplify Data Protection
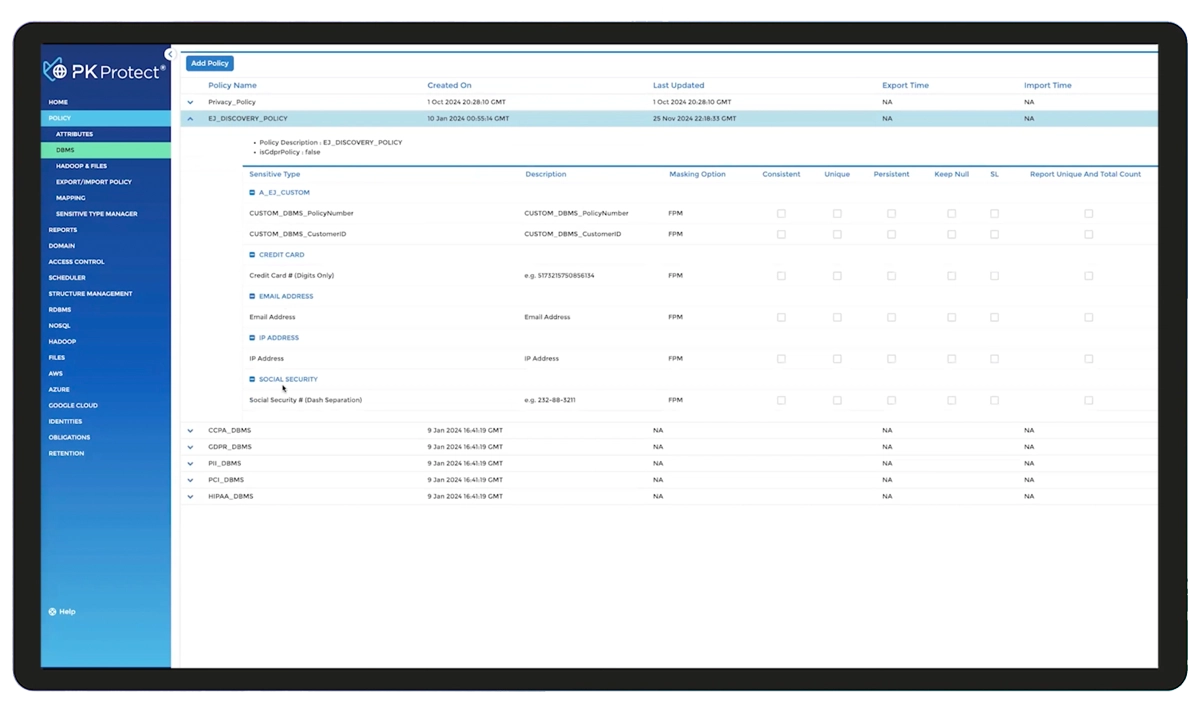
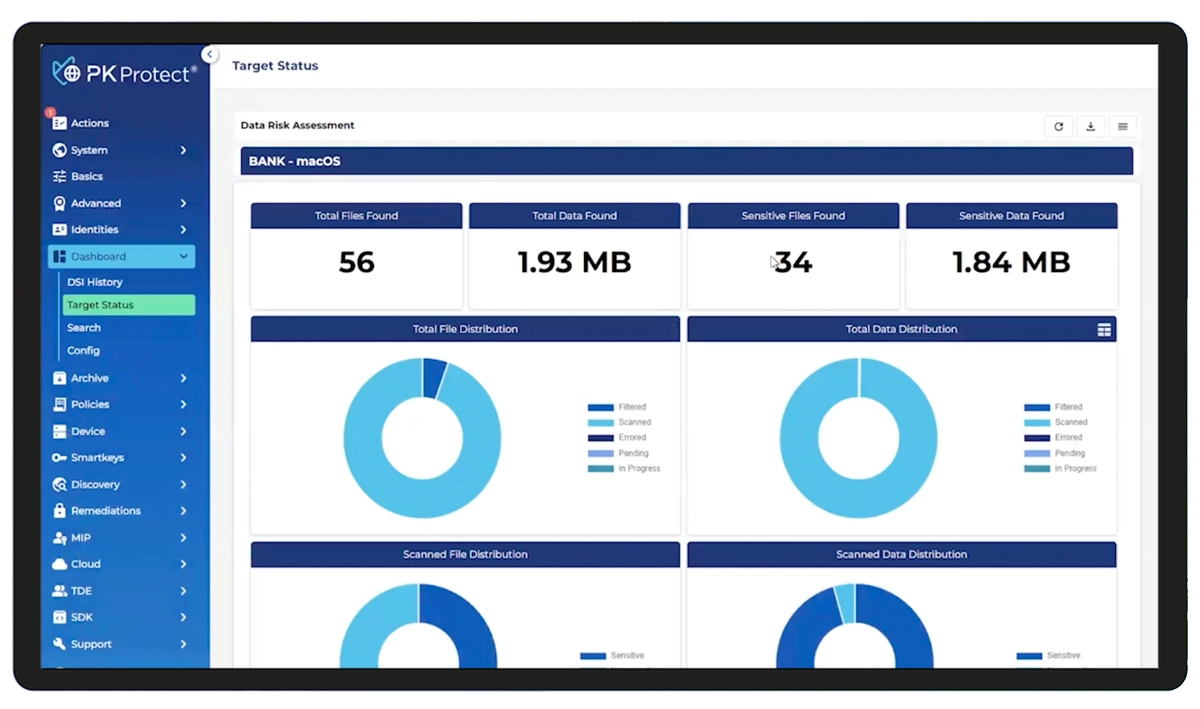
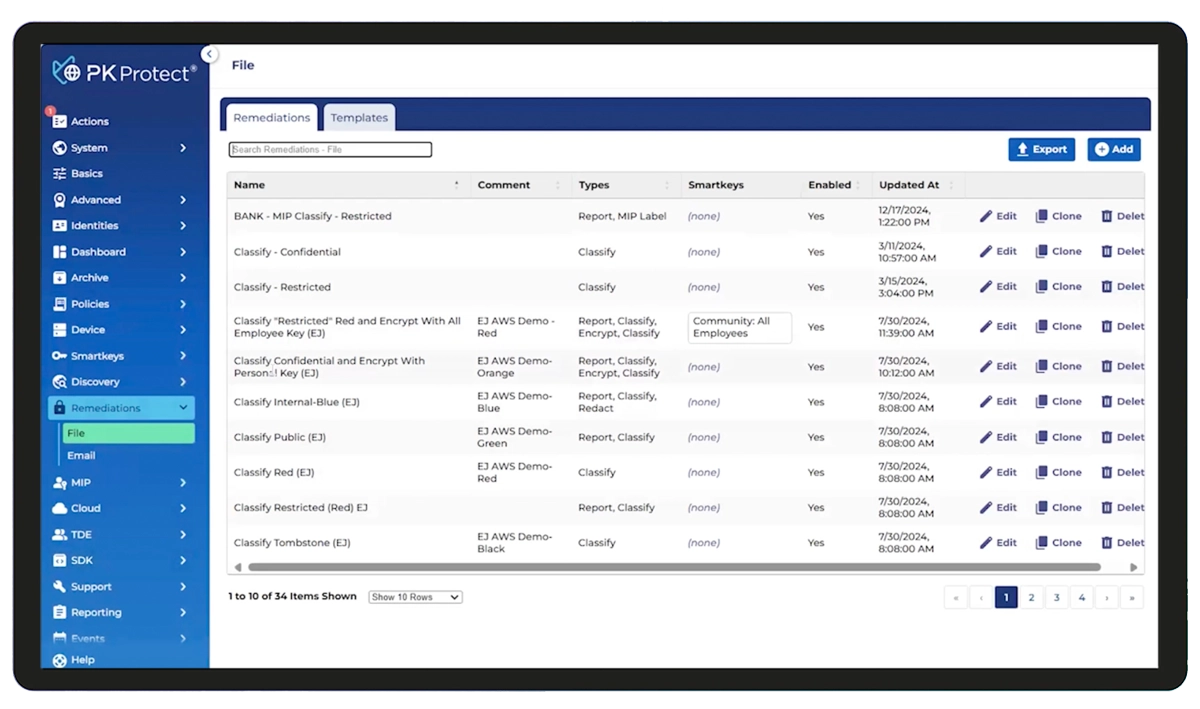
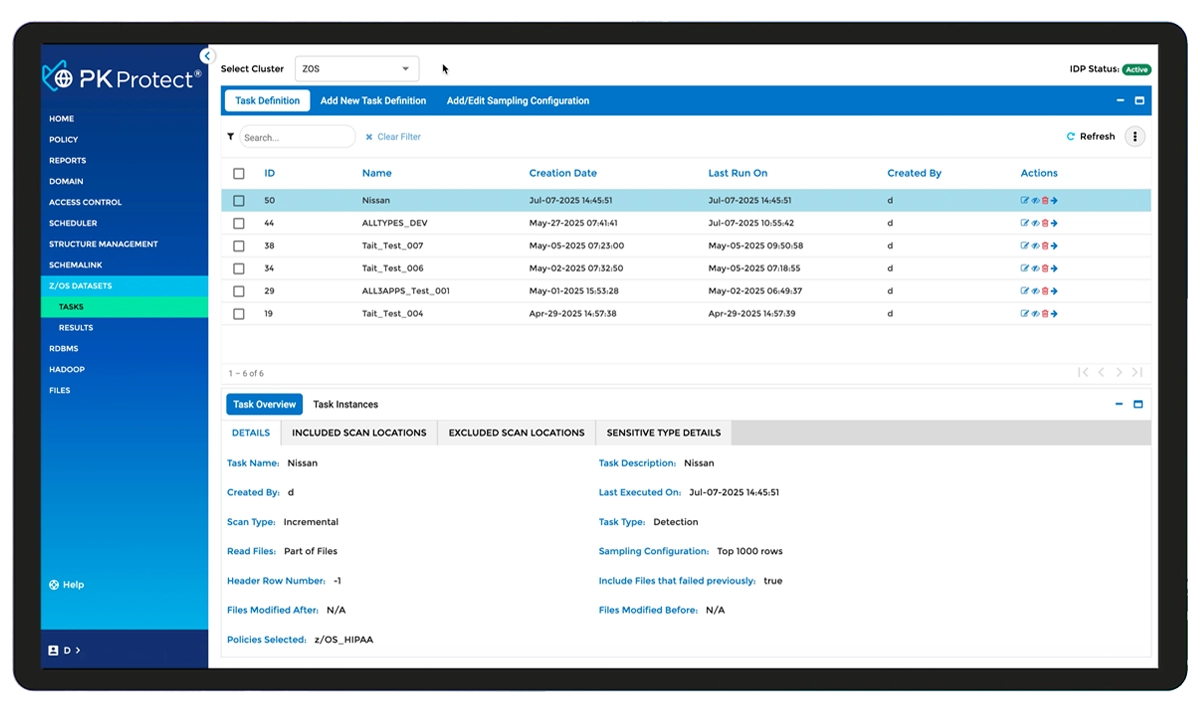
PK Protect provides the control businesses need to address complex data security challenges. With nearly 40 years of expertise in data security, PKWARE helps organizations discover and protect sensitive data across the enterprise—whether on endpoints, servers, SharePoint, OneDrive, the cloud, hybrid cloud, databases, data lakes, and mainframes. Through powerful automation and policy-driven controls, PK Protect enables enterprises to mitigate risk, maintain compliance, and securely use and share data without disrupting business operations.
What Customers Have to Say About PK Protect

“Data protection is going to continue to be important. And given that we operate at a global scale, we have to stay on top of that. This is why we are making investments in technology and working with partners like PKWARE.”

“I have had an excellent overall experience with PKWARE, from the initial implementation and training to the ongoing support. The continued assistance is truly appreciated. PK Protect is a powerful solution backed by exceptional support.”

“With PKWARE’s data security technology, I have confidence that we are meeting our data compliance goals. The encryption enables us to protect all of our data across platforms.”