Enterprise data is complex. Protecting it doesn’t have to be.
Simplify security and compliance with the only AI platform that combines discovery with protection, wherever your data lives and moves.
Trusted By Leading Organizations for Over 40 Years
Continuous Protection and Compliance Across Your Enterprise
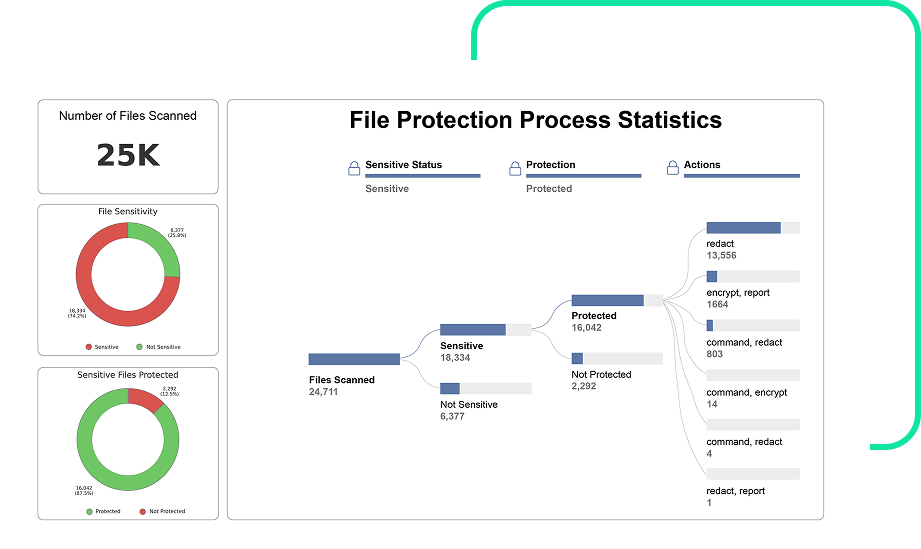
Leveraged by 21 of the top 25 US banks, PK Protect automatically discovers and protects data at enterprise scale, without complexity.
Ensure Compliance
Leveraged by 21 of the top 25 US banks, PK Protect automatically discovers and protects data at enterprise scale, without complexity.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation.

Data Breach Resilience
Leveraged by 21 of the top 25 US banks, PK Protect automatically discovers and protects data at enterprise scale, without complexity.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation.

Optimize Data Retention
Leveraged by 21 of the top 25 US banks, PK Protect automatically discovers and protects data at enterprise scale, without complexity.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation.

Use and Share Data Securely
Leveraged by 21 of the top 25 US banks, PK Protect automatically discovers and protects data at enterprise scale, without complexity.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation.

Compliance at Scale
FISERV, one of the largest financial services companies in the world, encrypts over 1 million files daily with PK Protect

Lorem ipsum dolor sit amet
consectetur elit.
Environments
Go beyond checking a box. Exceed complex regulatory requirements, pass audits, and avoid costly fines with ease.
Go beyond checking a box. Exceed complex regulatory requirements, pass audits, and avoid costly fines with ease.
Capabilities
Go beyond checking a box. Exceed complex regulatory requirements, pass audits, and avoid costly fines with ease.
Go beyond checking a box. Exceed complex regulatory requirements, pass audits, and avoid costly fines with ease.
PK Protect Provides Broad Platform Integration
Speak with a Data Security Expert
Explore how our Enterprise Data Security solution helps you discover, classify, and protect sensitive data, wherever it resides or moves. Connect with our experts for personalized insights and strategies tailored to your organization’s unique needs.


